PowerPoint Presentation
Scene 1 (0s)
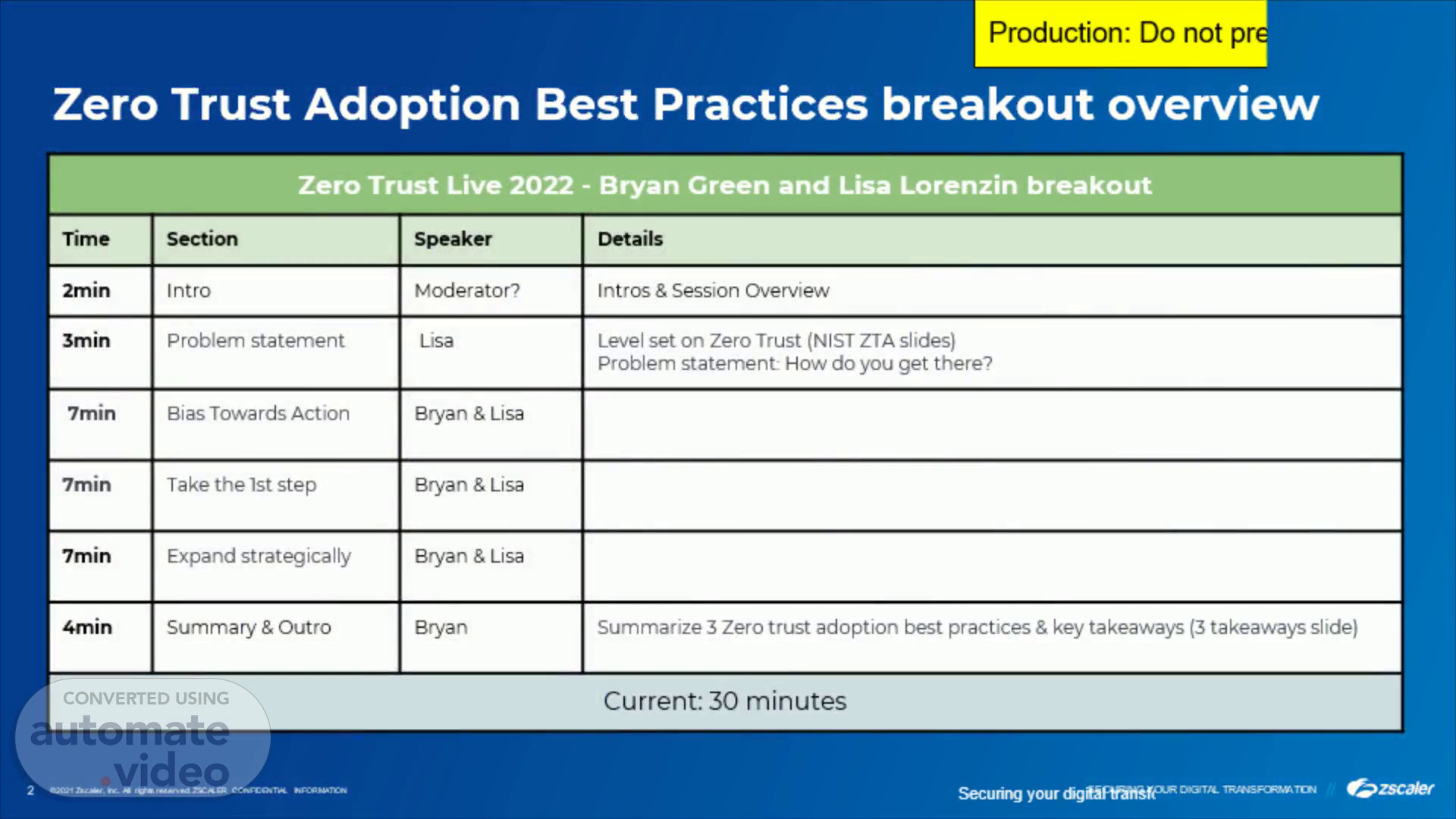
Securing your digital transformation. Zero Trust Adoption Best Practices breakout overview.
Scene 2 (25s)
Outline: Zero trust adoption best practices. [Bryan] Zero trust is hard, but have a bias towards action Avoid analysis paralysis , how to build conviction around outcomes Don’t over rotate on perfecting end state architecture that’s 24/36 months out. You have time Stop overthinking, start doing . Get some wins while you figure out the vision/strategy Gaining consensus across the organization, board, stakeholders [Lisa] Take the 1st step Don’t boil the ocean, otherwise you’ll never start In a hole? STOP digging Start with ZPA connectivity for architectural benefits (no external attack surface, no backhaul, visibility, etc) It’s not monolithic - do cloud-centric SASE thing first, will build the foundation to get to ZTA [Bryan] Expand strategically Quantify risk and prioritize accordingly. Use risk to drive prioritization Evolve to zero trust granularity one use case at a time , one user community at a time, etc. Step can be self-contained. Make progress towards the larger goal.
Scene 3 (1m 7s)
Lisa Lorenzin, Field CTO Bryan Green, Field CISO.
Scene 4 (1m 19s)
Meet the speakers. Lisa Lorenzin Field CTO, Americas.
Scene 5 (1m 29s)
Agenda. What is Zero Trust? Why is it difficult? How do we get there?.
Scene 6 (1m 37s)
CONTEXT. CONTEXT. TERMINATE Decrypt the traffic Inspect the data Identify the source Determine the destination.
Scene 7 (1m 56s)
Zscaler Zero Trust Exchange. Zscaler Zero Trust Exchange.
Scene 8 (2m 27s)
Difficult questions to answer. How do we pivot to Zero Trust? What are best practices for adoption? Where/how do we begin/start ? How do we get: Stakeholder buy-in and consensus? Board visibility and executive support What misconceptions and pitfalls should we avoid?.
Scene 9 (2m 42s)
Outcomes: Zero trust adoption best practices. Lisa - we’ll give you the TL;DR up front: three key takeaways from today’s conversation Bryan : Have a bias towards action . You’re on fire Lisa : Take the 1st step . Buy down risk, or at minimum, solve a painful very painful business problem (VPN, performance, remote access) Bryan : Expand strategically. It’s not monolithic. Zero Trust is a journey, plan accordingly..
Scene 10 (3m 4s)
Bias Towards Action. Lisa : Stop overthinking, start doing. Get some wins while you figure out the vision/strategy ZT can be overwhelming - so many vendors touting it; so many whitepapers, from analysts to govt; Look for low hanging fruit - where do you have a pain point? Common entry points are security risk (exposed attack surface, over-privileged access, third parties), user experience (backhaul, latency, complexity), cost (technical debt, expensive network infrastructure) Start small, ensure success, build credibility Bryan, how did this play out for you? work out the bugs/kinks, operationalize Bryan : Really understand use cases; have rigor around outcomes #ScopeCreep #ShinyNewThings.
Scene 11 (3m 34s)
Bias Towards Action. Bryan : Avoid analysis paralysis, how to build conviction around architecture Lisa, how do we unstick customers? Lisa : no single right answer - you don’t have to get it perfect on the first try Not monolithic - need an architecture that’s flexible enough to accommodate different levels of maturity, will increase confidence Bryan : Solutioning by democracy or crowdsourcing is problematic… too many chefs in kitchen.. Constructive consensus.. Guardrails.. Clear ownership model.. At the end, who owns the specific deliverables… No ownership without empowerment.. Resources.. Discipline and governance with Project Management.. How to escalate blockers, who makes decisions, how you’re tracking progress. Steering committee vs PCT.
Scene 12 (4m 3s)
Bias Towards Action. Lisa : Gaining consensus across the organization, board, stakeholders Dept of NO, infosec seen as a business inhibitor Moving towards zero trust removes brittleness and friction of mismatch between network layer controls and user-to-app needs New flexibility means you can accelerate existing initiatives and enable new ones Increased business intelligence - dept of KNOW Bryan, what was most effective for you in building consensus? Bryan : Building consensus: start with the WHY. effectively communicate how these changes will improve security outcomes and reduce risk Map KRD’s to capabilities, demonstrate risk reduction outcomes.
Scene 13 (4m 29s)
Take the 1st step. Bryan : Lisa, we’ve agreed to have a bias towards, how do we get started? Lisa : It’s not monolithic With apologies to William Gibson, “Zero trust is here, it’s just not evenly distributed” Do cloud-centric SASE thing first, will build the foundation to get to ZTA Start with ZPA connectivity for architectural benefits (no external attack surface, no backhaul, visibility, etc) That will give you visibility into user activity and workflows Strong foundation for identifying priorities and building towards a larger strategic goal.
Scene 14 (4m 54s)
Take the 1st step. Lisa : Bryan, what else do we need to do? Bryan : Stop making investments in legacy tech Use renewals as an opportunity to revisit tech. Meet current needs? Effective? Achieve business outcomes? Directionally aligned with Corp/Security strategy? Many of the tools we’re using today (firewall, VPN) worked really well a decade ago, aren’t best suited for today’s world of cloud and mobility Sunk cost fallacy - consider the cost of your technical debt (capex in appliances, dedicated connections; opex in configuration, management, troubleshooting) Lisa (chimes in): Don’t boil the ocean, otherwise you’ll never start Once you’ve identified that low-hanging fruit, make sure you understand how it fits into the larger plan - but don’t take on too much at once! You don’t have to have every answer upfront - may need to do application discovery, may need to improve your user groupings in your IAM Start with what you have and build from there.
Scene 15 (5m 32s)
Take the 1st step. Bryan : Many of the tools we’re using today (firewall, VPN) worked really well a decade ago, aren’t best suited for today’s world of cloud and mobility Sunk cost fallacy - consider the cost of your technical debt (capex in appliances, dedicated connections; opex in configuration, management, troubleshooting) Lisa (chimes in): Yeah, w hen you’re in a hole, STOP digging Don’t just keep trying to stretch your existing network-centric controls into use cases they don’t serve well If you were designing a solution from scratch to meet your needs both today and in the future , would you use yesterday’s technology?.
Scene 16 (5m 59s)
Expand Strategically. Lisa : You have a bias towards action, you’ve gotten a quick win - how do you keep the momentum and transition from tactical to strategic? Bryan : Quantify risk and prioritize accordingly Identify your individual use cases, their drivers, urgency Work with app owners / stakeholders to figure out their concerns (or what they don’t know!) Communicate challenges of current state and benefits of transformation KRD’s, Risk Management, quantifying risk.
Scene 17 (6m 20s)
Expand Strategically. Lisa : Evolve to zero trust granularity gradually One use case at a time, one user community at a time, etc. Each use case may require differing levels of control / context Leverage the tools you already have, identify gaps #ecosystem You may be fully prepared for some uses, need more info for others, and that’s okay! Can do serially or in parallel, depending on urgency and resources Crawl, walk, run methodology Bryan : You don’t have to do it alone Pro Services & Staff augmentation… you’re not alone, you may NOT have the expertise Build and align to a Mutual delivery plan (MDP).
Scene 18 (6m 48s)
Expand Strategically. Lisa : Each step can be self-contained, but works towards the larger goal Instead of multiple independent / uncoordinated projects Build momentum along the way Sanmina story - extended ZT to B2B for one use case, other stakeholders saw the benefits, everyone wanted to jump on “Victim of his own success” - had to figure out how to accelerate deployment Bryan, want to kick off the summary for us?.
Scene 19 (7m 8s)
Action Bias Avoid analysis paralysis You’re on ? Doing > Overthinking Quick wins.
Scene 20 (7m 27s)
Thank you!.