Scene 1 (0s)
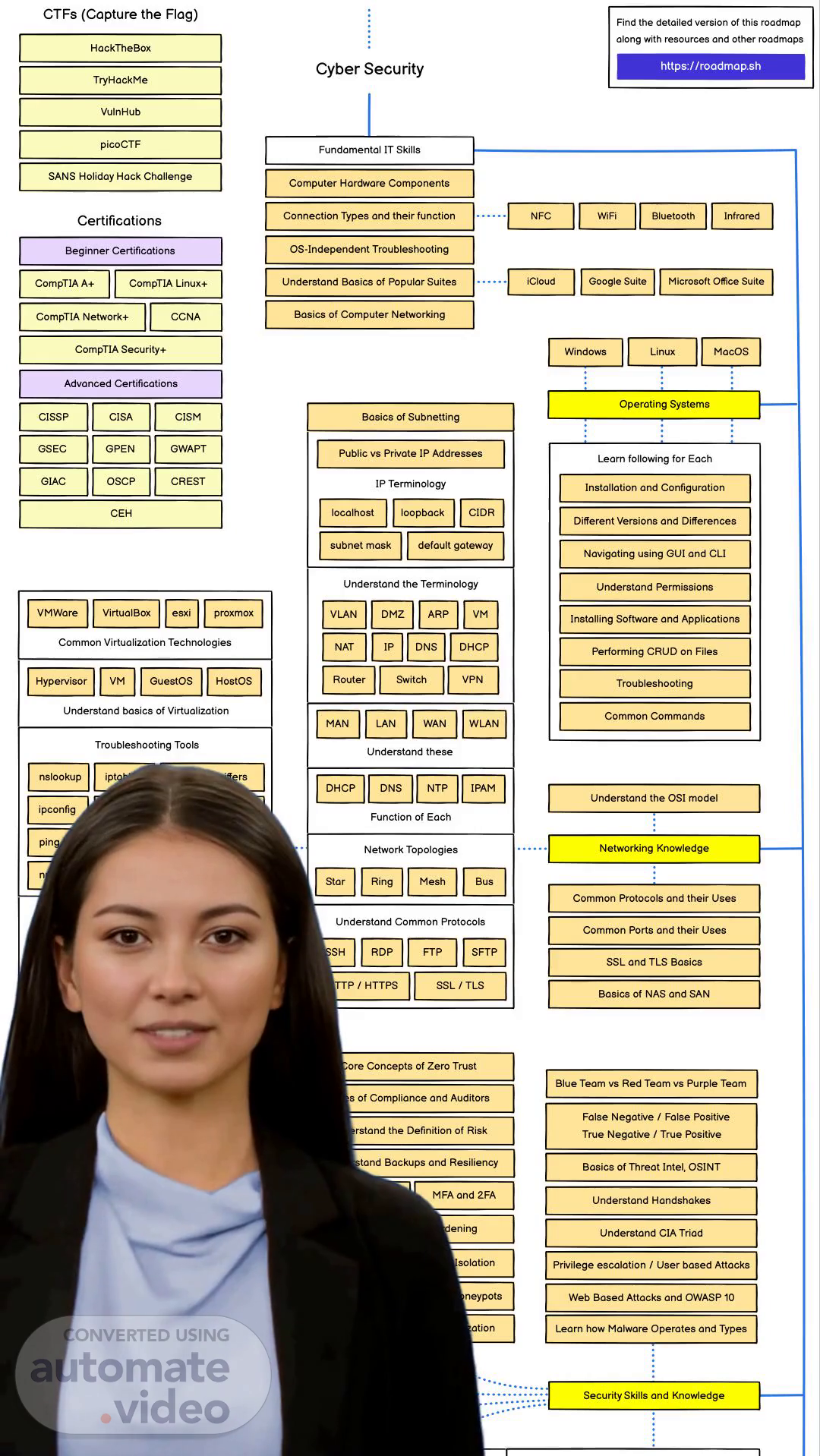
[Virtual Presenter] CTFs, or Capture the Flag competitions, involve completing various challenges and tasks related to cyber security, such as troubleshooting, understanding computer networking, and using common hacking tools. Find the detailed version of this roadmap along with resources and other roadmaps HackTheBox, https://roadmap.sh, Cyber Security, TryHackMe, VulnHub, picoCTF, Fundamental IT Skills, SANS Holiday Hack Challenge, Computer Hardware Components, Infrared, Bluetooth, NFC, WiFi, Connection Types and their function, Certifications, OS-Independent Troubleshooting, Beginner Certifications, Understand Basics of Popular Suites, iCloud, Google Suite, Microsoft Office Suite, CompTIA A+, CompTIA Linux+, Basics of Computer Networking, CompTIA Network+, CCNA, CompTIA Security+, Linux, MacOS, Windows, Advanced Certifications, Operating Systems, CISSP, CISA, CISM, Basics of Subnetting, GSEC, GPEN, GWAPT, Public vs Private IP Addresses, Learn following for Each, OSCP, GIAC, CREST, IP Terminology, Installation and Configuration, localhost, loopback, CIDR, CEH, Different Versions and Differences, subnet mask, default gateway, Navigating using GUI and CLI, Understand the Terminology, Understand Permissions, VMWare, VirtualBox, esxi, proxmox, VLAN, DMZ, ARP, VM, Installing Software and Applications, Common Virtualization Technologies, NAT, IP, DNS, DHCP, Performing CRUD on Files, Router, Switch, VPN, Hypervisor, VM, GuestOS, HostOS, Troubleshooting, Understand basics of Virtualization, Common Commands, MAN, LAN, WAN, WLAN, Troubleshooting Tools, Understand these, nslookup, iptables, Packet Sniffers, DHCP, DNS, NTP, IPAM, Understand the OSI model, ipconfig, netstat, Port Scanners, Function of Each Protocol, Analyzers, ping, dig, arp, Networking Knowledge, Network Topologies, nmap, route, tcpdump, tracert, Star, Mesh, Ring, Bus, Common Protocols and their Uses, Authentication Methodologies, Understand Common Protocols, Common Ports and their Uses, Kerberos, LDAP, SSO, SSH, FTP, RDP, SFTP, SSL and TLS, Basics, Certificates, Local Auth, RADIUS, HTTP/HTTPS, SSL/TLS, Basics of NAS and SAN, Understand Common Hacking Tools, Core Concepts of Zero Trust, Understand Common Exploit Frameworks, Blue Team vs.